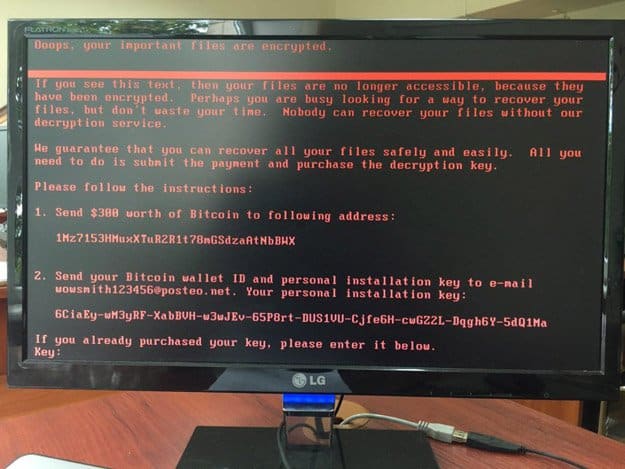
Yesterday another ransomware attack made its presence felt across the globe. Petya, which is a variant of WannaCry, was first detected in Ukraine. It then quickly infected systems in Spain, Germany, Israel, the UK, Netherlands and the US.
What is Petya?
Petya ransomware encrypts the master boot records of infected Windows computers, making affected machines unusable. Early reports indicate that the ransomware exploits vulnerabilities in Server Message Block (SMB). This is identical in nature to WannaCry's approach.
US-CERT encourages users and administrators to review the US-CERT article on the Microsoft SMBv1 Vulnerability and the Microsoft Security Bulletin MS17-010. It should be noted the patch does not apply to Windows XP systems. In other words, if you still run XP, help is not on the way.
Like WannaCry, Petya spreads rapidly through networks that use Microsoft Windows. Petya has impacted a number of industries and firms:
- US Healthcare (Heritage Valley Health System, Nuance Transcription services and others)
- Governments
- Pharmaceutical giant Merck
- Shipping giant Maersk
- The Chernobyl nuclear reactor
- Food giant Mondelez
- Law firm DLA Piper
HHS Issues Petya Mitigation Steps
This morning the Department of Health and Human Services (HHS) sent an email titled: Cyber Notice: Current International Ransomware Campaign.
In it, they recommended the following steps to mitigate Petya:
- Educate users on common Phishing tactics to entice users to open malicious attachments or to click links to malicious sites.
- Patch vulnerable systems with the latest Microsoft security patches
- Verify perimeter tools are blocking Tor .Onion sites
- Use a reputable anti-virus (AV) product whose definitions are up-to-date to scan all devices in your environment in order to determine if any of them have malware on them that has not yet been identified. Many AV products will automatically clean up infections or potential infections when they are identified.
- Monitor US-CERT for the latest updates from the U.S. government.
- Utilize HPH Sector ISAC and ISAO resources.
Our Thoughts on HHS Recommendations
In my opinion, the recommendations coming from HHS come up short. Here's why:- The one percent. While user education on detecting phishing attacks will remain important, I believe there is a segment of business users that will open any email attachment. This holds true regardless of training and is due to the subconcious mind as it relates to work. A small segment of users, about 1%, will open all work emails and their attachments. In other words, they subconsciously correlate opening work email, no matter what's in it or who it's from, to doing their job properly.
- Reactive approach. Evidence clearly supports the notion that users do not update their Windows systems often enough. This is also a reactive measure. New variants from Petya will continue have a window of time to do damage. If the window is always open, it will always be used (path of least resistance).
- AV is also reactive. Anti-virus systems are also reactive measures. In addition, Petya infects the Master Boot Record (MBR), thus rendering the infected machine incapable to booting up in the first place. AV can't run unless the computer boots.
In a nutshell, I believe a new way of thinking is in order.
A Better Approach to Ransomware: Proactive Measures
Since ransomware primarily enters a network via email phishing attacks containing macros, we believe the time has come to take a hard look at fundamental aspects of email security.
Here are our proactive recommendations on stopping Ransomware:
- Block all Macros. We believe the business downside from allowing email attachments containing macros now outweighs its upsides. In August 2016, we took the decisive step of quarantining all incoming email that contained macros. Not a single Paubox customer has ever been infected or even had a ransomware email enter their corporate inboxes.
- Enable Google Safe Browsing. Google Safe Browsing is a blacklist service provided by Google that provides lists of URLs for web resources that contain malware or phishing content. It's free to use and can be configured to for use with email security scanning.
- Nuclear option: Only use Macs. It's something to think about.
I outlined these best practices in a presentation I gave at NIST last week.
SEE RELATED: Effective Anti-Phishing Strategies and Exercises - FISSEA 2017 Conference [SlideShare]
Subscribe to Paubox Weekly
Every Friday we bring you the most important news from Paubox. Our aim is to make you smarter, faster.

 Hoala Greevy
Hoala Greevy



