
According to our HIPAA Breach Reports, email is the top threat vector in healthcare. But this holds true across all industries, according to Verizon’s 2021 Data Breach Investigations Report. This is easy to see for any IT security professional, with common cyberattacks like malware being delivered via email 94% of the time. If that’s not bad enough, bad actors are constantly modifying and changing attacks faster than most detection systems can keep up with. The numbers can be overwhelming, but your organization has a fighting chance if you have the right email security strategy in place to ward off threats to your inbox.
In this guide we'll cover:
- What is email security
- Why you need an effective email security strategy
- The top-3 most common attacks
- Email security best practices
What is email security?
Many people think email security is nothing more than spam filtering. But as attacks have evolved, your strategies should move beyond anti-spam filters too. The current approach is more complex compared to what it was a couple of decades ago. It does include spam filtering, but it also encompasses other measures for securing access to an account and email content, including predictive analysis of incoming emails and preventing interception of email messages by unauthorized parties during transit. In this guide, we'll focus on email security against inbound threats. Other secure email strategies like email encryption and data loss prevention (DLP) are discussed in detail in other posts.
Why do you need an effective email security strategy?

At 50 years old, email is often regarded as an outdated form of digital communication. The "next big thing" like text messaging, group chatting, and video calling are all celebrated as email replacements for contact and collaboration. However, email has yet to be dethroned and remains a valuable tool because of its ubiquity. Practically anyone who has access to the internet has an email address—you can’t sign up for most apps without one. Email can be sent to anyone, which is vitally important for business communication where you can't force parties to be on the same messaging platform and still make communication easy and painless. Organizations across various industries rely on business email as their primary means of reaching out to employees, customers, and other stakeholders. Old-fashioned as it is, email has over 4 billion users, or half of the world population. Cybersecurity threats can spread through other channels, but hackers know they can get more victims if they go through email. It’s the reason why email is the top threat vector even in 2021. But gone are the days when annoying junk mail was the primary issue with your inbox. Though it still gets its fair share of victims, messages from Nigerian princes offering you millions of dollars if you share your bank details are basic. Now, you have to watch out for threats that are hard to spot and even harder to eradicate.
The global average cost of a data breach is $3.92 million."
Malicious emails often look authentic, and without additional verification, their fraudulent nature is easy to miss. Once they start wreaking havoc, it can be challenging to mitigate the damage because attacks usually evolve faster than patches can be made. The result is often a data breach. According to IBM’s Cost of a Data Breach Study, the global average cost of a data breach is $3.92 million. That’s a huge cost for any organization, but especially for small- and medium-sized businesses (SMBs). But since it’s just the average, the figure can go as high as hundreds of millions. For their 2015 data breach that compromised the personal health information (PHI) of almost 79 million people, health insurance provider Anthem was legally obligated by a federal court to pay a class action settlement of $115 million, the largest one to date for a HIPAA violation. And that data breach started from a spear-phishing email sent to a few Anthem employees. The financial loss alone is significant, but a data breach also causes another loss money can’t buy—reputation. Organizations spend years building a good name, but one data breach can ruin it. It’s difficult to regain stakeholders’ trust after it has been lost. Not all organizations can withstand the fallout. An effective email security strategy must be proactive, not reactive. The goal being simply to prevent attacks before they can cause costly harm.
What are the most common email threats?
Before you can win, you need to know what you’re up against.
Phishing emails
Disguised as legitimate messages from reputable entities such as financial institutions, government agencies, or major retailers, phishing emails ask recipients to send confidential information or open an attachment containing malware. The recipients, not realizing they are being duped, do what is requested without a second thought.Spear-phishing emails
Although they have the same structure and intent as the regular kind of phishing, spear-phishing emails are more targeted. They’re not sent out to the masses; rather, they’re delivered to a specific group or person to whom the messages are relevant. For example, the emails can be made to look as if they’re sent out to customers of a bank or employees of a company, like what happened with Anthem. Because of the level of personalization involved, they’re more difficult to detect.Display name spoofing
Another form of trickery is display name spoofing which involves changing the sender’s display name so that the email seems to come from a trusted source. Cybercriminals count on the fact that many people don’t bother verifying a sender's email address when they get a message. Sometimes, the email address is also spoofed, adding another layer to the scam.Ransomware
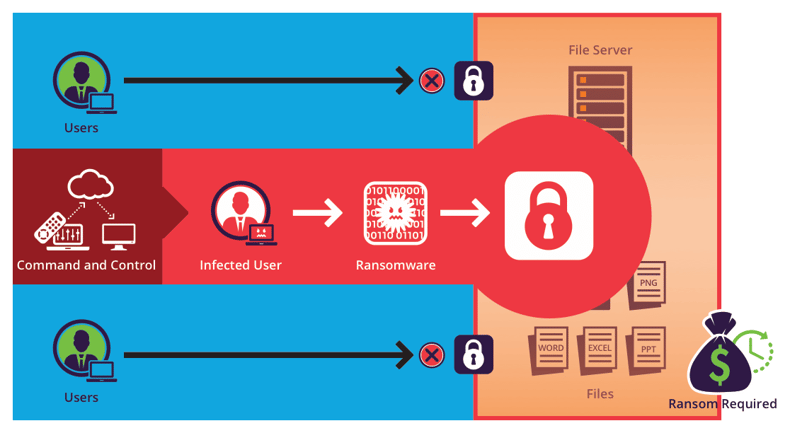
A subset of malware, ransomware blocks access to a system (or a device in some cases) until a ransom is paid in bitcoin or another untraceable method. Most payloads are delivered via an email attachment or link. Ransomware attacks have become more high profile of late and represent a growing concern for every organization. The US government has recently started uniting against ransomware attacks as well. As mentioned, the goal of email attacks is to get people to hand over sensitive data or to trick them into downloading malware. Hackers use the information they steal for nefarious purposes—selling it on the dark web’s black market, using it for identity theft, holding it for ransom, or using it to access financial accounts.
Email security best practices

Thankfully, it's not all doom and gloom. There are very real steps any organization can take to greatly improve their protection against email threats.
Build your wall and gateway
Automated processes are more secure and less prone to errors. Use technology to your advantage to prevent the vast majority of threats from reaching end-users. But you can do better than simple antivirus software; there are email security solutions like Paubox Email Suite Plus that analyze incoming emails for known threats and filter them accordingly. The best solutions have advanced threat detection features like Paubox’s ExecProtect which stops display name spoofing emails from reaching users’ inboxes altogether. Paubox Email Suite Plus also comes with Zero Trust Email which requires an additional piece of evidence to authenticate an email sender’s mail server before being delivered. An effective email security solution works in tandem with, and enhances, your existing business email platform such Microsoft 365 or Google Workspace.
Validate your email
Email authentication proves that a message came from your organization. This process decreases spoofing and phishing attempts, thus preventing attacks and protecting your brand. Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-Based Message Authentication, Reporting & Conformance (DMARC) are the three forms of email authentication. Inbound threat protection would be simpler if every organization adopted these standards, making legitimate emails easier to recognize.
Train your staff
Unfortunately, not all junk mail ends up in the spam folder or quarantine because no software is perfect and bad actors are coming up with new variations every minute. This means a few questionable emails may still get through from time to time, so employees should know how to assess messages using simple steps, such as hovering over links to verify the destination URLs before clicking or refraining from opening email attachments from unvetted sources. Training isn't just a one-time item to check-off at new hire orientation either. Regular training, reminders, and even internal phishing campaigns have all proven to help keep employees vigilant against threats to avoid falling victim to The Overconfidence Dilemma.
Be ready to react
Though an effective email security strategy should be preventive, you have to be ready to spring into action in case of a successful attack. Your organization’s response will depend on the nature of the attack, but speed is critical. Your response can range from isolating affected systems and containing the situation, to notifying customers and assessing the damage.
SEE ALSO: 5 Business Best Practices For Email Security
Summary
People won’t stop using email anytime soon. It has been around for 50 years and shows no sign of being phased out. That means bad actors will continue to wage war on your inbox, so it’s best to invest in building a robust email security strategy to protect your organization.
How Paubox can help
Paubox Email Suite Plus prevents email threats from hitting the inbox with robust spam filtering and email security against ransomware, malware, and phishing attacks.
Subscribe to Paubox Weekly
Every Friday we bring you the most important news from Paubox. Our aim is to make you smarter, faster.




