
- What is Display Name Spoofing?
- Why is Display Name Spoofing Dangerous?
- How does Paubox solve Display Name Spoofing?
What is Display Name Spoofing?
Display Name Spoofing is a relatively new type of phishing attack that exploits:- Current email trends
- Incumbent email security vendors
With the growing adoption of email security tools like SPF, DKIM, and DMARC, bad actors are finding it harder to spoof domain names.
Instead, their attacks have migrated to a more simple approach: Changing the display name of the sender to a C-level executive in the target organization.
Why is Display Name Spoofing Dangerous?
Three words: Money. Authority. Sophistication.
Money: Display Name Spoofing is dangerous because the scams being carried out are financial in nature.
Here's a few examples we've heard about that are being successfully perpetrated:
- Re-routing bank accounts of C-level executives for payroll deposits
- Purchase requests for thousands of dollars of Gift Cards
Authority: The Display Name Spoof attack always purports to come from a person of authority in the company.
When this is coupled with:
- The fact that at least 70% of all email is now read from a smartphone.
- By default, email apps on a smartphone only show the Display Name of the sender. If you want to see the actual email address, further action (i.e. friction) is required.
The net effect is that if you see an email from your boss on your phone, you'll probably open it immediately, not bothering to think about the actual email address it came from.
Sophistication: Lastly, Display Name Spoofing attacks are leveling up in sophistication. Long gone are the days of typos, deposed Nigerian princes, and run-on sentences.
Examples of advanced sophistication include:
- No attachments to scan
- No links to inspect
- Many are sent from valid Gmail, AOL, and Yahoo accounts
- The Display Name of the sender is from a C-level executive (CEO, CFO, COO, etc).
- The email is short, to the point, and often introduces urgency via a time crunch
- They often insert phrases like "Sent from my iPad" at the bottom. This is done to give the appearance it was authentically composed at a moment's notice
Long story short, Display Name Spoofing attacks are working. The good guys are losing the battle so far in 2019.
How does Paubox solve Display Name Spoofing?
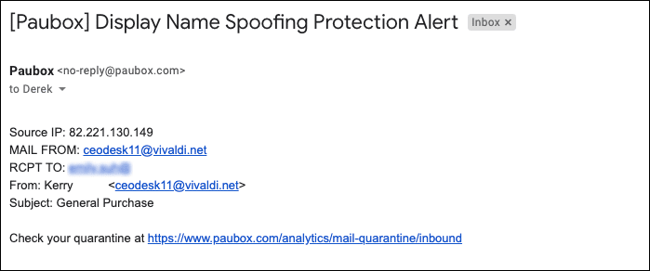
Display Name Spoofing Attack stopped by Paubox
Paubox Email Suite Plus already goes a step further than traditional email security products with features like protection against phishing, spam and ransomware attacks.
Unique benefits not found elsewhere in the market include:
To address Display Name Spoofing, we put our heads down and built a solution that immediately integrates with Paubox.
In a nutshell, here's how it works:
- We work with our customer to compile a list of their executives being impersonated.
- The list includes email addresses they use to communicate with staff.
- If an incoming email matches an executive's name and is not from a recognized email address, it gets immediately quarantined.
It's simple, effective, and it works. For example, we stopped 50 Display Name Spoof attacks from reaching a customer in a single day. Rather than modify the body of the email to alert the end user it was an external email, we prevented it from even reaching their inbox.
Lastly, we can see from a recent Reddit thread that allowing the Display Name Spoofing attack to reach the inbox, regardless if it's been modified to have a disclaimer at the top, is not the correct approach.
We believe the market will agree with us on this.
Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.



 Hoala Greevy
Hoala Greevy


