3 min read
Danger alert: Criminals can spread malware through fax machines
Arianna Etemadieh September 5, 2018

According to research conducted by Check Point, fax machines have an dangerous vulnerability. It doesn't matter how large or small your organization is, nor does it matter if you are only a fax-owning civilian.
All a cybercriminal needs is a fax number to exploit a flaw in fax protocol. This flaw could enable the hacker to potentially gain complete control of your company or home network. And fax numbers are not hard to find, considering they are still present on websites and business cards.
The fax machine might seem outdated to most organizations, but in healthcare, banking, and other regulated industries, the fax is still alive and well. In fact, there are over 45 million fax machines still used globally today, and 17 billion faxes are sent every year.
READ MORE: Fax Machines Are Terrible for Healthcare – Here's Why (New Data)
Check Point dubbed their groundbreaking research "Faxploit". Here's what you need to know.
What is Faxploit?
Check Point Software Technologies is a leading provider of cybersecurity solutions globally. At the Defcon hacker event in Las Vegas, Check Point presented their research for a flaw they dubbed, "Faxploit." The Check Point team conducted their experiment on the popular HP Officejet Pro All-in-One fax printers. They noted some security flaws when it came to these fax machines and eventually successfully exploited them. Once exploited, the Check Point team was able to create a backdoor into a network that the fax machine was connected to, and then steal the information through the fax.
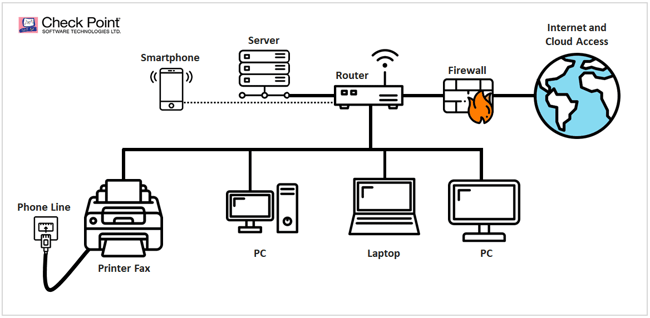
Check Point shared their findings with HP, who quickly resolved the issue with a security software patch. However, the researchers warn that the same fax protocols used by HP Officejet Pro All-in-One fax printers are also used by many other fax machines and multi-function printers. Even online fax services like fax2email use similar fax protocols, making it also susceptible to hacking. To make matters worse, the research team believe there are tens of millions of vulnerable fax machines currently in use today.
How Faxploit works
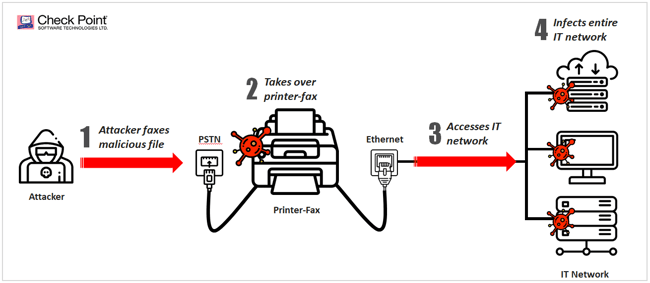
Faxploit takes effect in a series of steps:
- The cybercriminal obtains the organization's fax number from their website or business card
- The cybercriminal then sends a "specially created image file" via fax to the victim
- Fax vulnerabilities allow malware, such as ransomware, cryptominers or spyware, to be embedded into the code of the image file
- The fax machine decodes this malicious code and uploads it to it's memory
- From there, the malware can breach sensitive data such as PHI or spread across any networks the fax machine is connected to
Check Point researchers were able to get full control of the fax machine at one point and send malware to a vulnerable PC.
That is one serious security flaw. “Many companies may not even be aware they have a fax machine connected to their network, but fax capability is built into many multi-function office and home printers,” Yaniv Balmas, Group Manager, Security Research at Check Point, shared. “This groundbreaking research shows how these overlooked devices can be targeted by criminals and used to take over networks to breach data or disrupt operations. “It’s critical that organizations protect themselves against these possible attacks by updating their fax machines with the latest patches and separating them from other devices on their networks,” Balmas continued. “It’s a powerful reminder that in the current, complex fifth-generation attack landscape, organizations cannot overlook the security of any part of their corporate networks.”
Getting rid of the fax altogether
When a generation is no longer taught how to use a fax machine, it's time to let it go.
Yes, fax machines are still alive because regulated industries like healthcare still rely on them. But the healthcare industry is notoriously outdated. They still use pagers, which were also recently discovered to have a fatal security flaw. If only there was an electronic way to send messages… oh wait, there is! Introducing Paubox's seamless HIPAA compliant email.
What do we mean by seamless? We mean no extra encrypt buttons, no passwords, no making sure you entered a "1" before a fax number. Simply upload any PHI attachments, attach them to an email and send. Easy as that. Paubox encrypts all emails and replies by default so you don’t have to. Even better – you can send an encrypted email as you normally would.
There’s no need for additional training for your staff and no change in user behavior. This is because Paubox puts the user experience first for both senders and recipients.
We provide military-grade encryption features without the hassle of extra steps. Paubox also includes security features such as robust SPAM filtering that identifies malware and phishing attacks and has protocols against ransomware.
With seamless integration into business email platforms like Google Workspace, Microsoft 365 and Microsoft Exchange, you can keep your email address and domain as well. When we say there will be no change in user behavior, we mean it.
To assure your recipients that the email you sent is encrypted, they will see a neat little digital signature at the footer of your email saying that your email was encrypted for their safety and security by Paubox.
Subscribe to Paubox Weekly
Every Friday we bring you the most important news from Paubox. Our aim is to make you smarter, faster.


![Who uses fax machines anymore? Healthcare does [video]](https://www.paubox.com/hubfs/Imported_Blog_Media/printer-958139_1920-3.jpg)