REPORT
2025 healthcare email security report
Key insights from 180 email-related healthcare breaches and actionable steps to protect your organization.

REPORT
2025 healthcare email security report
Key insights from 180 email-related healthcare breaches and actionable steps to protect your organization.

Top takeaways
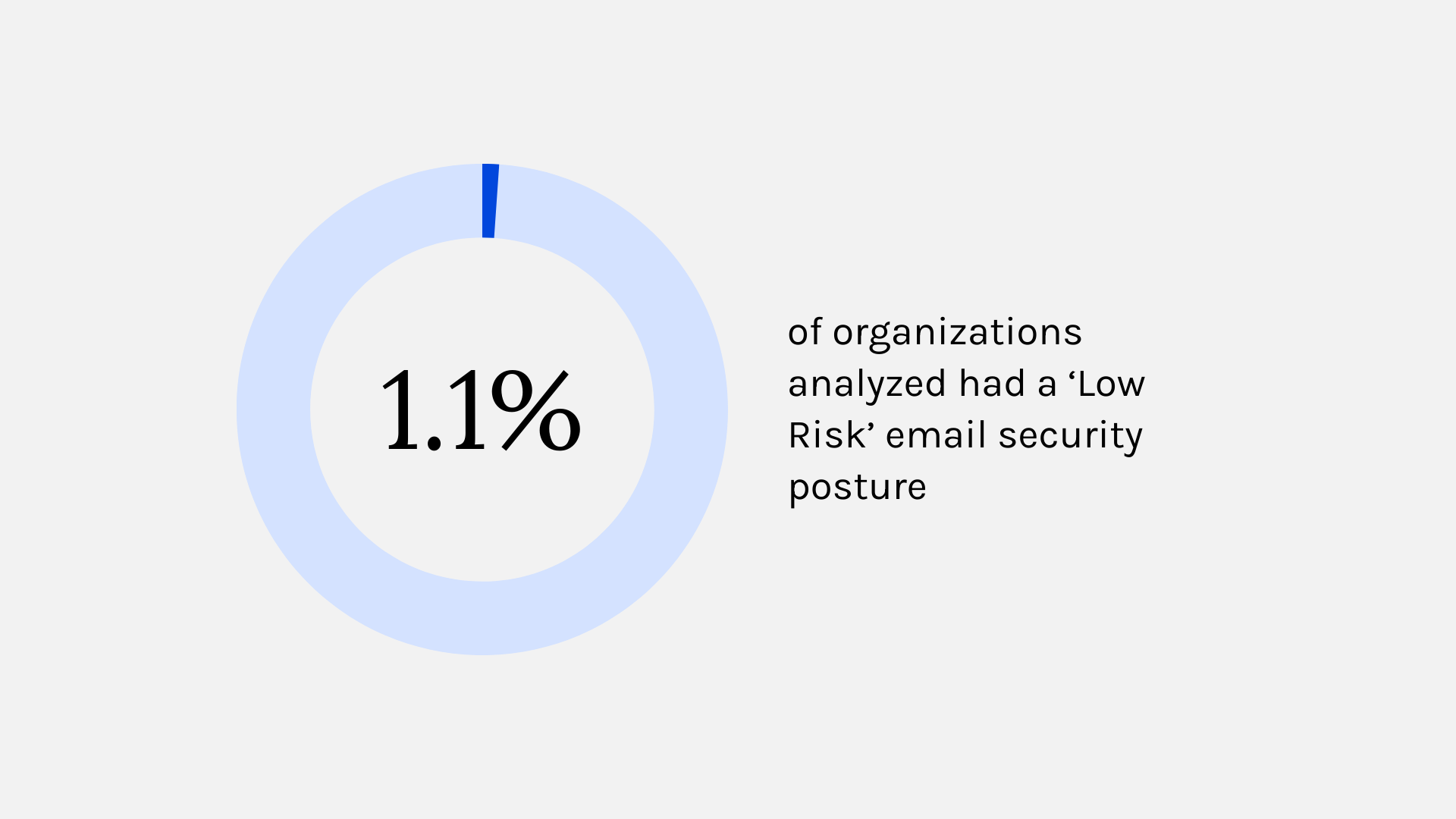
What the data reveals about rural healthcare's growing cybersecurity gap, and where leaders must act next.
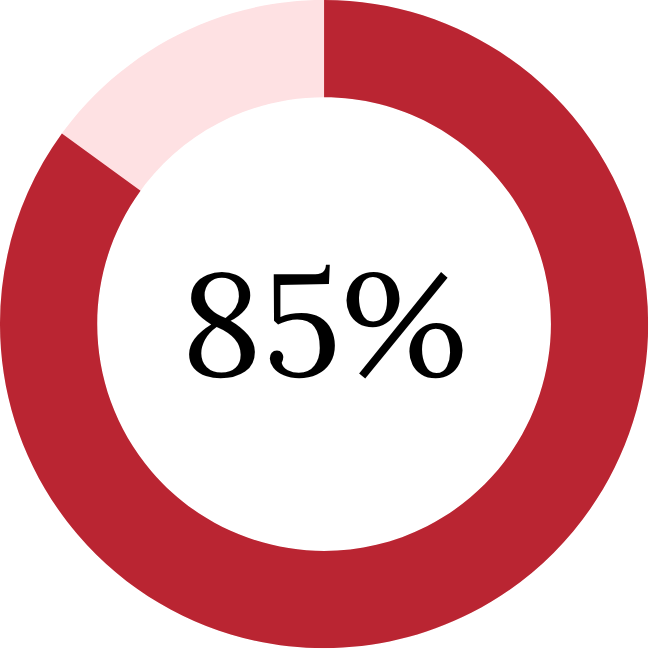
85% of rural healthcare IT leaders report their current infrastructure can't support advanced email security
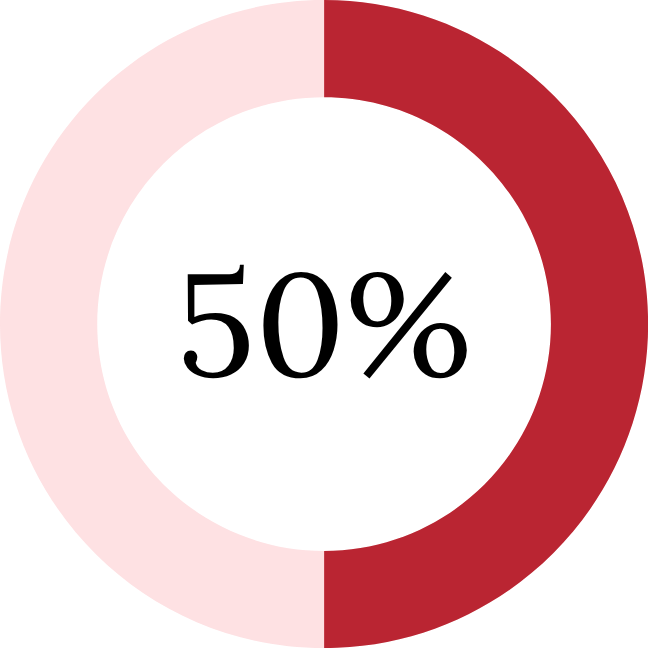
50% of rural IT leaders cite budget limitations as a top barrier to adopting HIPAA-compliant email, nearly double their urban peers
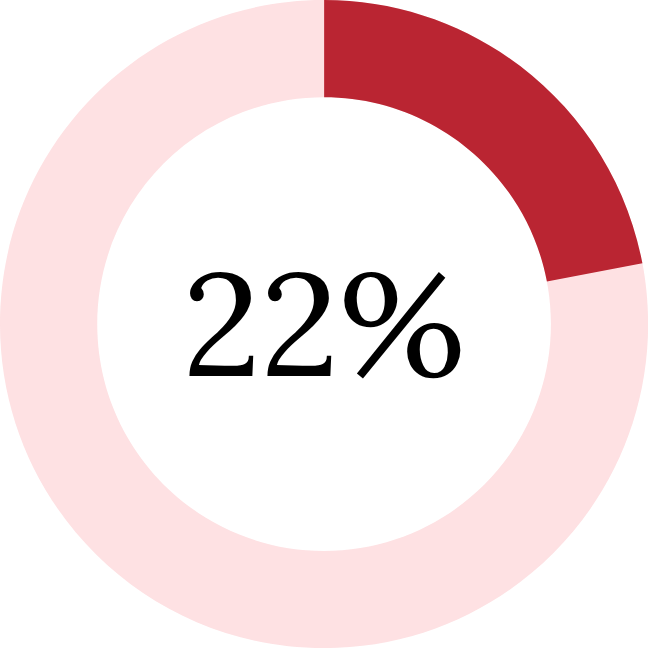
Rural orgs are lagging their urban counterparts by 22% in adopting AI-driven threat detection

73% of rural leaders admit they struggle to maintain HIPAA compliance due to a lack of staff and funding
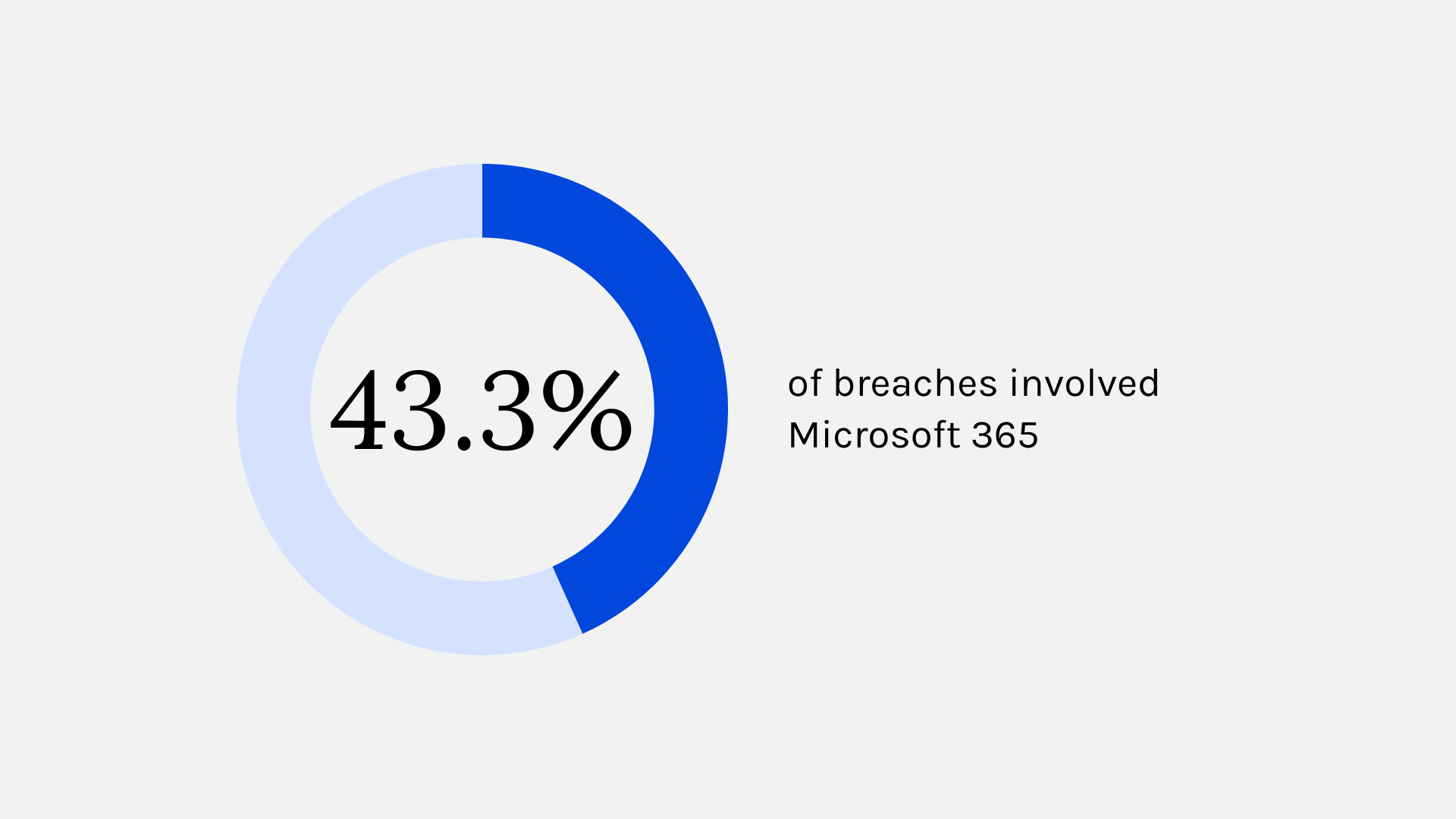
.png)
.png)












