PAUBOX EMAIL API
HIPAA compliant email API for developers
Easy setup, integrate in minutes

5,000+ customers trust Paubox to secure 99 million emails every month

.png?width=768&height=268&name=COVE_Corporate_Full-Color-768x268%20(2).png)
.png?width=400&height=140&name=simonmed-imaging-logo-400%20(2).png)

Set up in minutes
- Go to market faster with API libraries
- Clear documentation
- RESTful API and SMTP options available
- Top rated U.S. support
Deliver messages securely
- Include PHI and PII
- Emails delivered with TLS 1.2 or higher
- Business associate agreement included
- HITRUST CSF certified
Get your apps to market faster
—
Start sending email notifications, reminders and updates without reinventing the wheel.
- Drive innovation without worrying about HIPAA compliance
- Reduce lengthy development timelines
- Improve and optimize message deliverability
- Track results on the Paubox analytics dashboard or utilize webhooks to pull event data into a third-party dashboard
- Paubox Email Suite
- Paubox Marketing
- Paubox Email API
How many users do you have?
Encryption
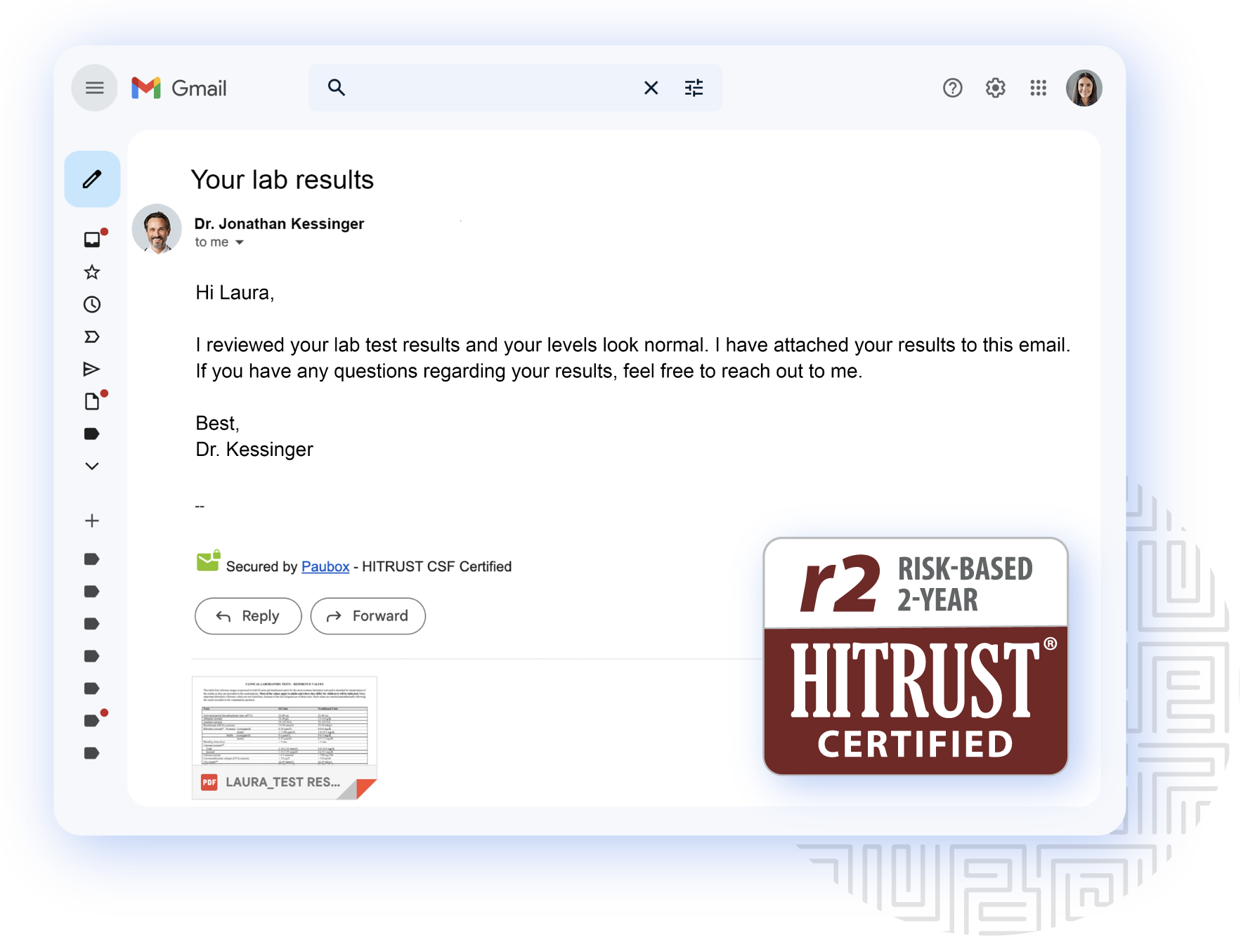
Securely send protected health information (PHI) via email
Patented blanket TLS encryption ensures that PHI sent via email is always encrypted.Integrates with major business email platforms
Paubox integrates directly with Google Workspace, Microsoft 365, and Microsoft Exchange. Send HIPAA compliant email directly from your existing email provider with no change in behavior required.Emails delivered directly to the inbox
Recipients read encrypted emails directly in their inboxes. No cumbersome portal required for recipients.Send secure calendar invites
Send secure, HIPAA compliant calendar invites directly from Microsoft Outlook and Google Workspace. No plugins or apps to install.Secure contact form
Add a secure contact form to your website as a Paubox hosted link.Optimized email deliverability
Maximizes email deliverability and avoids outbound email ending in spam folders by updating your SPF record and configuring DKIM and DMARC protocols.Dashboard access
Manage your email quarantine, whitelist/blacklist rules, and more from the Paubox dashboard. Grant varying access levels to your team.Compliance
HIPAA compliant
Maintain the highest privacy and data protection with our HIPAA seal of compliance by Compliancy Group.HITRUST CSF certified
Safeguard your data with Paubox Email Suite, which has been HITRUST CSF certified for its rigorous controls.Business associate agreement
Under HIPAA, organizations that use a service provider to process PHI on their behalf must put in place a business associate agreement with that service provider. Paubox includes BAAs with all accounts.Security
TLS protocols 1.2 & 1.3
As per NSA guidance, Paubox supports only TLS 1.2 and TLS 1.3. The following obsolete protocols are not supported: SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1.Two-factor authentication
Require authentication beyond a username and password when logging into your Paubox account.U.S. data centers
Rely on our cloud-based, redundant infrastructure with 99.99%, uptime. Customer data is stored encrypted at-rest and solely in U.S data centers.Analytics
Real-time analytics
Comprehensive email analytics, mail logs, ruleset access, and quarantine.Email reports
Daily or weekly email reports on usage, analytics, patterns, and alerts sent directly to your inbox. These reports make it easy to quickly demonstrate value to upper management.Support
Help center
Learn how to use Paubox products quickly with concise how-to articles, and step-by-step instructions.Phone support
Our customer success team is available by phone for extended hours, Monday through Friday, to assist with any technical or support issu our customers might have.Inbound email security
ExecProtect
Patented protection from display name spoofing attacks.Zero Trust Email
Zero Trust Email requires an additional layer of authentication before an email reaches your inbox.DomainAge
Immediately quarantine email coming from recently registered domain names.Blacklist bot powered by AI
Quickly blacklist malicious email addresses.Malware and virus protection
Ransomware protection
Google SafeSearch
Robust spam filtering
Data loss prevention
Email archiving
Take compliance and disaster recovery to a new level, with emails and attachments stored in the Paubox cloud.Email DLP
Data loss prevention for both inbound and outbound email traffic for your organization.Advanced features
Voicemail transcription
On the fly, HIPAA compliant voicemail transcription for audio email attachments.Optional add-on
Frequently asked questions
Paubox works with Google Workspace, Microsoft 365, and Microsoft Exchange. Be sure your email host provides a business associate agreement.
Yes, you can use your smartphone and your favorite email apps.
Paubox can also easily be setup on tablets and smartwatches with no proprietary apps or downloads needed.
Yes, all attachments are encrypted.
Paubox supports attachments up to 50MB.
A sender is defined as one email address such as you@yourcompany.com. Aliases and email groups are not counted.
Plan: Start start scale enterprise start
$179 / month $399/month $599 / month $179 / month
-
Up to 3 team members
-
Unlimited storage
-
Unlimited affiliates & leads
-
Private label client portal
-
Up to 600 active clients
-
All our core features
-
Up to 12 team members
-
Unlimited storage
-
Unlimited affiliates & leads
-
Private label client portal
-
Up to 1200 active clients
-
All our core features
-
Up to 24 team members
-
Unlimited storage
-
Unlimited affiliates & leads
-
Private label client portal
-
Up to 2400 active clients
-
All our core features
-
Unlimited affiliates & leads
-
Unlimited storage
-
Unlimited affiliates & leads
-
Private label client portal
-
Up to 300 active clients
-
All our core features
($ Annually)
Plan: Start
$179 / month
-
Up to 3 team members
-
Unlimited storage
-
Unlimited affiliates & leads
-
Private label client portal
-
Up to 300 active clients
-
All our core features





How many contacts do you have?
$0 per month
Billed Annually
1 - 100 contacts
Campaigns
Send personalized email with PHI
Paubox enforces TLS encryption for every email campaign, so marketing teams can send personalized emails directly to patients’ inboxes that include PHI.Drag and drop builder
Quickly and easily create beautiful emails with our intuitive design builder.Dynamic text
Insert dynamic smart text based on custom contact data fields.Image and file manager
Easily organize and securely store images and filesSend unlimited emails
Pricing is based on contacts stored, not emails sent in a month.Optimized email deliverability
Maximizes email deliverability and avoids outbound email ending in spam folders by updating your SPF record and configuring DKIM and DMARC protocols.Contacts
Audience segmentation
Manage contacts and and create audience lists based on custom field data.Securely upload and store contacts and data
Contact data is housed securely within the platform.Custom data fields
Create and import custom contact data fields.Compliance
HIPAA compliant
Maintain the highest privacy and data protection with our HIPAA seal of compliance by Compliancy Group.HITRUST CSF certified
Safeguard your data with Paubox Email Suite, which has been HITRUST CSF certified for its rigorous controls.Business associate agreement
Under HIPAA, organizations that use a service provider to process PHI on their behalf must put in place a business associate agreement with that service provider. Paubox includes BAAs with all accounts.TLS protocols 1.2 & 1.3
As per NSA guidance, Paubox supports only TLS 1.2 and TLS 1.3. The following obsolete protocols are not supported: SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1.Two-factor authentication
U.S. data centers
Rely on our cloud-based, redundant infrastructure with 99.99%, uptime. Customer data is stored encrypted at-rest and solely in U.S data centers.Marketing Automation
Workflow builder
Create advanced drip campaigns with an easy-to-use visual builderAutomation triggers
Automate workflow journeys based on user actionAnalytics
Performance reporting
Track overall performance of email campaigns, track specific link clicks, and download reports.Email link click tracking
See which readers clicked on your links.Data visualizations for reporting
Visual reporting for a quick glance view of campaign performance.API endpoints to integrate data with external reporting tools
Automatically pull analytics and results into an external reporting dashboard.Integrations, Admin and Support
API connections to CRM/EHR/EMRs
Connect to a customer or patient database via API to automatically sync contact data.U.S.-based support team
Support team available to assist with implementation, training and support.Phone support
Our customer success team is available by phone for extended hours, Monday through Friday, to assist with any technical or support issues our customers might have.Help center documentation
Learn how to use Paubox products quickly with concise how-to articles, and step-by-step instructions.Frequently asked questions
Paubox is a leader in secure email that empowers developers and marketers to drive meaningful and lasting engagements with their customers. With Paubox Marketing, you can create, send, and track one-to-many messages. Because it’s backed by our cloud-based SMTP provider, which acts as an email delivery engine, you can send email without the cost and complexity of maintaining your own email servers. It takes the complication out of email creation so you can quickly and easily produce professional emails to achieve your business goals.
Once you create and verify your account, you can store up to 100 contacts for free, using Paubox Marketing. Need more? You can easily upgrade to our standard plan at anytime.
We require all of our customers to verify their accounts. This helps to safeguard your account and maintain deliverability for you and all of our customers.
How many emails do you send per month?
$0 per month
Billed Annually
0-300 emails
API
Programmatically send HIPAA compliant email
Customizable API with multiple client libraries.Optimized email deliverability
Maximizes email deliverability and avoids outbound email ending in spam folders by updating your SPF record and configuring DKIM and DMARC protocols.Dynamic email templates
Create templated messages that can be customized with dynamic data.Compliance
HITRUST CSF certified
Our solutions have met key regulatory requirements, industry defined requirements, and appropriately manage risk.Security
TLS protocols 1.2 & 1.3
As per NSA guidance, Paubox supports only TLS 1.2 and TLS 1.3. The following obsolete protocols are not supported: SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1.Blanket TLS email encryption
Maximize the security of your organization’s emails by enforcing TLS secure email for every email sent and every campaign. No cumbersome portal login required for recipients. Blanket TLS email encryption is our unique, patented solution.Two-factor authentication
Require authentication beyond a username and password when logging into your Paubox account.U.S. data centers
Rely on our cloud-based, redundant infrastructure with 99.99%, uptime. Customer data is stored encrypted at-rest and solely in U.S data centers.Analytics
Real-time analytics
Comprehensive email analytics, mail logs, ruleset access, and quarantine.Webhooks
Webhooks alert you when a message has been delivered, has a temporary failure, or has a permanent failure.Resources
REST API
Use our RESTful APIs that are built on HTTPS and return JSON for clear implementation.SMTP API
Deliver your email via our servers instead of your own client or server.Comprehensive client libraries
Code in your preferred language with open source libraries and use cases in Node.JS, Ruby, Python, PHP, Ruby on Rails, Java, Perl, and C#.API docs
Expedite end-to-end integration time with our robust API documentation.Support
Help center
Learn how to use Paubox products quickly with concise how-to articles, and step-by-step instructions.Phone support
Our customer success team is available by phone for extended hours, Monday through Friday, to assist with any technical or support issue our customers might have.Frequently asked questions
Using Paubox Email API for our system notifications saves our customers time, saves them trouble, and gives them more information.

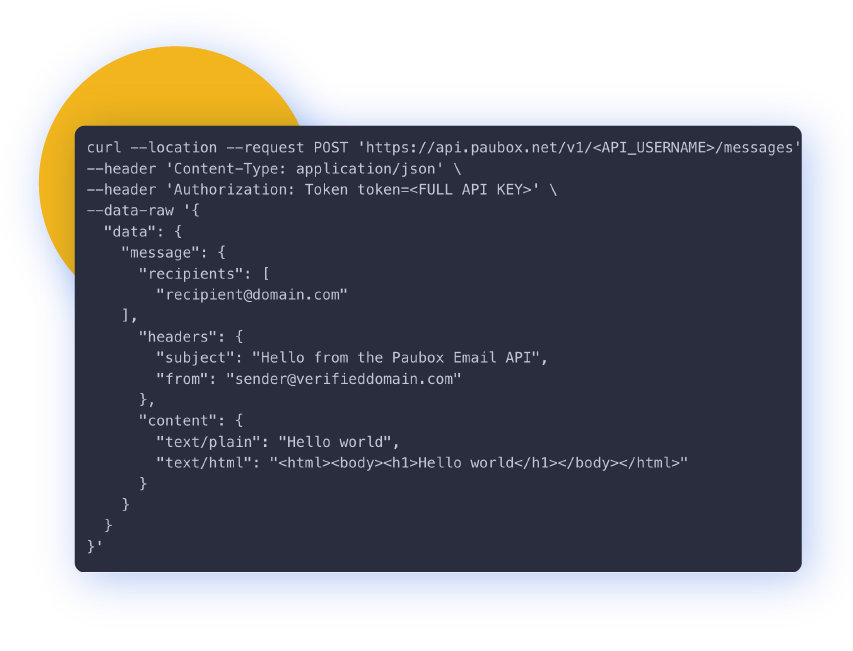
Integrate in minutes
Deliver secure email faster with our REST APIs and SMTP libraries
- API libraries
- Clear developer documentation
- Send 300 emails per month for free
// Send secure email using the Paubox JavaScript/Node.js Library
// https://github.com/Paubox/paubox-node
"use strict";
require('dotenv').config();
const pbMail = require('paubox-node');
const service = pbMail.emailService(); var options = {
from: 'sender@domain.com',
to: ['recipient@example.com'],
subject: 'Testing!',
text_content: 'Hello World!',
html_content: '<html><head></head><body><h1>Hello World!</h1></body></html>',
}
var message = pbMail.message(options)
service.sendMessage(message)
.then(response => {
console.log("Send Message method Response: " + JSON.stringify(response));
}).catch(error => {
console.log("Error in Send Message method: " + JSON.stringify(error));
});
# Send secure email using the Paubox Ruby Library
# https://github.com/Paubox/paubox_ruby
require 'Paubox'
require 'json'
require 'mail'
message = Mail.new do
from 'you@yourdomain.com'
to 'someone@somewhere.com'
cc 'another@somewhere.com'
subject 'HIPAA-compliant email made easy'
text_part do
body 'This message will be sent securely by Paubox.'
end
html_part do
content_type 'text/html; charset=UTF-8'
body '<h1>This message will be sent securely by Paubox.</h1>'
end
delivery_method Mail::Paubox
end
message.deliver!
=> {"message"=>"Service OK", "sourceTrackingId"=>"2a3c048485aa4cf6"}
message.source_tracking_id
=> "2a3c048485aa4cf6"
# Send secure email using the Paubox Ruby on Rails Extended Gem
# https://github.com/Paubox/paubox-rails
class UserMailer < ApplicationMailer
def welcome_email
@user = params[:user]
@url = user_url(@user)
delivery_options = { allow_non_tls: true }
mail(to: @user.email,
subject: "Welcome!",
delivery_method_options: delivery_options)
end
end
# Send secure email using the Paubox Python 3 Library
# https://github.com/Paubox/paubox-python3
import paubox
from paubox.helpers.mail import Mail
from config import Config
with open("config.cfg") as config_file:
paubox_config = Config(config_file)
paubox_client = paubox.PauboxApiClient(paubox_config.PAUBOX_API_KEY,
paubox_config.PAUBOX_HOST)
recipients = ["recipient@example.com"]
from_ = "sender@yourdomain.com"
subject = "Testing!"
content = {"text/plain": "Hello World!"}
mail = Mail(from_, subject, recipients, content)
response = paubox_client.send(mail.get())
print(response.status_code)
print(response.headers)
print(response.text)
// Send secure email using the Paubox C# Library
// https://github.com/Paubox/paubox-csharp
static SendMessageResponse SendMessage()
{
Message message = new Message();
Content content = new Content();
Header header = new Header();
message.Recipients = new string[] { "someone@domain.com",
"someoneelse@domain.com" };
header.From = "you@yourdomain.com";
message.Cc = new string[] { "cc-recipient@domain.com" };
message.Bcc = new string[] { "bcc-recipient@domain.com" };
header.Subject = "Testing!";
header.ReplyTo = "reply-to@yourdomain.com";
content.PlainText = "Hello World!";
message.Header = header;
message.Content = content;
SendMessageResponse response = EmailLibrary.SendMessage(message);
return response;
}
static SendMessageResponse SendMessage()
{
Message message = new Message();
Content content = new Content();
Header header = new Header();
message.setRecipients(new String[] { "someone@domain.com",
"someoneelse@domain.com" });
header.setFrom("you@yourdomain.com");
message.setCc(new String[] { "cc-recipient@domain.com" });
message.setBcc(new String[] { "bcc-recipient@domain.com" });
header.setSubject("Testing!");
header.setReplyTo("reply-to@yourdomain.com");
content.setPlainText("Hello World!");
message.setHeader(header);
message.setContent(content);
EmailInterface email = new EmailService();
SendMessageResponse response = email.SendMessage(message);
return response;
}
// Send secure email using the Paubox PHP Library
// https://github.com/Paubox/paubox-php
<!--?php
require_once __DIR__ . '/vendor/autoload.php';
$dotenv = Dotenv\Dotenv::create(__DIR__);
$dotenv->load();
$paubox = new Paubox\Paubox();
$message = new Paubox\Mail\Message();
$content = new Paubox\Mail\Content();
$content->setPlainText("Hello World");
$header = new Paubox\Mail\Header();
$header->setSubject("Testing!");
$header->setFrom("sender@domain.com");
$recipients = array();
array_push($recipients,'recipient@example.com');
$message->setHeader($header);
$message->setContent($content);
$message->setRecipients($recipients);
$sendMessageResponse = new Paubox\Mail\SendMessageResponse();
$sendMessageResponse = $paubox->sendMessage($message);
print_r($sendMessageResponse);
# Send secure email using the Paubox Perl Library
# https://github.com/Paubox/paubox-perl-sdk
use strict;
use warnings;
use Paubox_Email_SDK;
my $messageObj = new Paubox_Email_SDK::Message(
'from' => 'sender@domain.com',
'to' => ['recipient@example.com'],
'subject' => 'Testing!',
'text_content' => 'Hello World!',
'html_content' => '<html><head></head><body><h1>Hello World!</h1></body></html>',
);
my $service = Paubox_Email_SDK -> new();
my $response = $service -> sendMessage($messageObj);
print $response;
// Send secure email using the Paubox JavaScript/Node.js Library
// https://github.com/Paubox/paubox-node
"use strict";
require('dotenv').config();
const pbMail = require('paubox-node');
const service = pbMail.emailService(); var options = {
from: 'sender@domain.com',
to: ['recipient@example.com'],
subject: 'Testing!',
text_content: 'Hello World!',
html_content: '<html><head></head><body><h1>Hello World!</h1></body></html>',
}
var message = pbMail.message(options)
service.sendMessage(message)
.then(response => {
console.log("Send Message method Response: " + JSON.stringify(response));
}).catch(error => {
console.log("Error in Send Message method: " + JSON.stringify(error));
});
# Send secure email using the Paubox Ruby Library
# https://github.com/Paubox/paubox_ruby
require 'Paubox'
require 'json'
require 'mail'
message = Mail.new do
from 'you@yourdomain.com'
to 'someone@somewhere.com'
cc 'another@somewhere.com'
subject 'HIPAA-compliant email made easy'
text_part do
body 'This message will be sent securely by Paubox.'
end
html_part do
content_type 'text/html; charset=UTF-8'
body '<h1>This message will be sent securely by Paubox.</h1>'
end
delivery_method Mail::Paubox
end
message.deliver!
=> {"message"=>"Service OK", "sourceTrackingId"=>"2a3c048485aa4cf6"}
message.source_tracking_id
=> "2a3c048485aa4cf6"
# Send secure email using the Paubox Ruby on Rails Extended Gem
# https://github.com/Paubox/paubox-rails
class UserMailer < ApplicationMailer
def welcome_email
@user = params[:user]
@url = user_url(@user)
delivery_options = { allow_non_tls: true }
mail(to: @user.email,
subject: "Welcome!",
delivery_method_options: delivery_options)
end
end
# Send secure email using the Paubox Python 3 Library
# https://github.com/Paubox/paubox-python3
import paubox
from paubox.helpers.mail import Mail
from config import Config
with open("config.cfg") as config_file:
paubox_config = Config(config_file)
paubox_client = paubox.PauboxApiClient(paubox_config.PAUBOX_API_KEY,
paubox_config.PAUBOX_HOST)
recipients = ["recipient@example.com"]
from_ = "sender@yourdomain.com"
subject = "Testing!"
content = {"text/plain": "Hello World!"}
mail = Mail(from_, subject, recipients, content)
response = paubox_client.send(mail.get())
print(response.status_code)
print(response.headers)
print(response.text)
// Send secure email using the Paubox C# Library
// https://github.com/Paubox/paubox-csharp
static SendMessageResponse SendMessage()
{
Message message = new Message();
Content content = new Content();
Header header = new Header();
message.Recipients = new string[] { "someone@domain.com",
"someoneelse@domain.com" };
header.From = "you@yourdomain.com";
message.Cc = new string[] { "cc-recipient@domain.com" };
message.Bcc = new string[] { "bcc-recipient@domain.com" };
header.Subject = "Testing!";
header.ReplyTo = "reply-to@yourdomain.com";
content.PlainText = "Hello World!";
message.Header = header;
message.Content = content;
SendMessageResponse response = EmailLibrary.SendMessage(message);
return response;
}
static SendMessageResponse SendMessage()
{
Message message = new Message();
Content content = new Content();
Header header = new Header();
message.setRecipients(new String[] { "someone@domain.com",
"someoneelse@domain.com" });
header.setFrom("you@yourdomain.com");
message.setCc(new String[] { "cc-recipient@domain.com" });
message.setBcc(new String[] { "bcc-recipient@domain.com" });
header.setSubject("Testing!");
header.setReplyTo("reply-to@yourdomain.com");
content.setPlainText("Hello World!");
message.setHeader(header);
message.setContent(content);
EmailInterface email = new EmailService();
SendMessageResponse response = email.SendMessage(message);
return response;
}
// Send secure email using the Paubox PHP Library
// https://github.com/Paubox/paubox-php
<!--?php
require_once __DIR__ . '/vendor/autoload.php';
$dotenv = Dotenv\Dotenv::create(__DIR__);
$dotenv->load();
$paubox = new Paubox\Paubox();
$message = new Paubox\Mail\Message();
$content = new Paubox\Mail\Content();
$content->setPlainText("Hello World");
$header = new Paubox\Mail\Header();
$header->setSubject("Testing!");
$header->setFrom("sender@domain.com");
$recipients = array();
array_push($recipients,'recipient@example.com');
$message->setHeader($header);
$message->setContent($content);
$message->setRecipients($recipients);
$sendMessageResponse = new Paubox\Mail\SendMessageResponse();
$sendMessageResponse = $paubox->sendMessage($message);
print_r($sendMessageResponse);
# Send secure email using the Paubox Perl Library
# https://github.com/Paubox/paubox-perl-sdk
use strict;
use warnings;
use Paubox_Email_SDK;
my $messageObj = new Paubox_Email_SDK::Message(
'from' => 'sender@domain.com',
'to' => ['recipient@example.com'],
'subject' => 'Testing!',
'text_content' => 'Hello World!',
'html_content' => '<html><head></head><body><h1>Hello World!</h1></body></html>',
);
my $service = Paubox_Email_SDK -> new();
my $response = $service -> sendMessage($messageObj);
print $response;
Why Paubox?
Drive app usage for
a better patient experience
Deliver personalized notifications and reminders that engage patients and other users.
Focus on your
product
You build. Let us maintain the HIPAA compliant email infrastructure.
Reduce risk
Every email sent is HIPAA compliant, every time. Paubox Email API is HITRUST CSF certified and offers a business associate agreement for all customers.
Get help when you need it
Paubox customer service is a best-in-class, US-based team who is available via email or phone.
How Paubox Email API works
01. Emails are sent via your app
Your application triggers an email to be sent with Paubox Email API
02. Emails get encrypted
Emails are seamlessly encrypted by Paubox servers with 128/256-bit AES encryption.
03. Protected in transit
Emails are protected while on their way to the recipient's inbox with TLS 1.2 encryption protocol and higher
04. No TLS 1.2+? No problem!
If the destination inbox can't receive encrypted email, then a secure link is delivered to view the message
Developer resources
Download software development kits and review instructions in the developer document portal.






