
Here's how to send HIPAA compliant emails and ensure patients' health information is secure and protected during communication.
HIPAA compliance is critical for healthcare organizations, and this article will help you understand the requirements for email and provide you with practical steps to achieve compliance.
You'll learn:
- Who needs to send HIPAA compliant email
- How HIPAA compliant email protects PHI
- Four steps to send HIPAA compliant emails
- Are Gmail, Microsoft 365, and others HIPAA compliant?
- HIPAA compliant email checklist
- Which emails should be HIPAA compliant?
- FAQs
- Other HIPAA rules around handling ePHI
Who needs to send HIPAA compliant email?
Covered entities and business associates should send HIPAA compliant emails. i.e., Any organization that handles and sends electronic protected health information (ePHI).
What are covered entities: Covered Entities can be institutions, organizations, or persons:
- Certain Healthcare Providers: Providers who submit HIPAA transactions, like electronic claims. Common examples are Doctors, Clinics, Psychologists, Dentists, Chiropractors, Nursing homes, and Pharmacies
- Health Plans: Health Insurance companies, HMOs, Employer-sponsored health plans, and Government programs that pay for healthcare (Medicare, Medicaid, and military and veterans’ health programs)
- Healthcare Clearinghouses: Organizations that process nonstandard health information to conform to standards for data content or format, or vice versa, on behalf of other organizations.
What are business associates: people or businesses that work with healthcare organizations and have access to ePHI, such as IT providers and medical billing companies, and attorneys working with covered entities.
Learn more:
How HIPAA compliant email protects PHI
What is PHI: According to the HIPAA Privacy Rule, "Individually identifiable health information" is information, including demographic data, that relates to:
- the individual's past, present or future physical or mental health or condition,
- the provision of health care to the individual, or
- the past, present, or future payment for the provision of health care to the individual, and that identifies the individual or for which there is a reasonable basis to believe it can be used to identify the individual."
Plainly put, PHI includes:
- Medical record number
- Unique identifying number
- An invoice with billing information
- An appointment reminder
- Blood test results
- Prescription information
- Payment history
- Account number
- Family members
As well as more common patient information, including:
- Name
- Phone number
- Email address
- Street address
- Zip code
- Birthdate
Why it matters: When PHI is transmitted electronically via email, there is a risk that unauthorized individuals could access it. Consequences for patients include identity theft, financial fraud, and even discrimination based on their medical history.
HIPAA compliant email safeguards patient privacy by utilizing encryption to ensure secure transmission of PHI over the internet, and access controls, which prevent unauthorized access. Adhering to these requirements enables covered entities and business associates to maintain patients' medical information confidentiality and security.
Learn more: What is protected health information (PHI)?
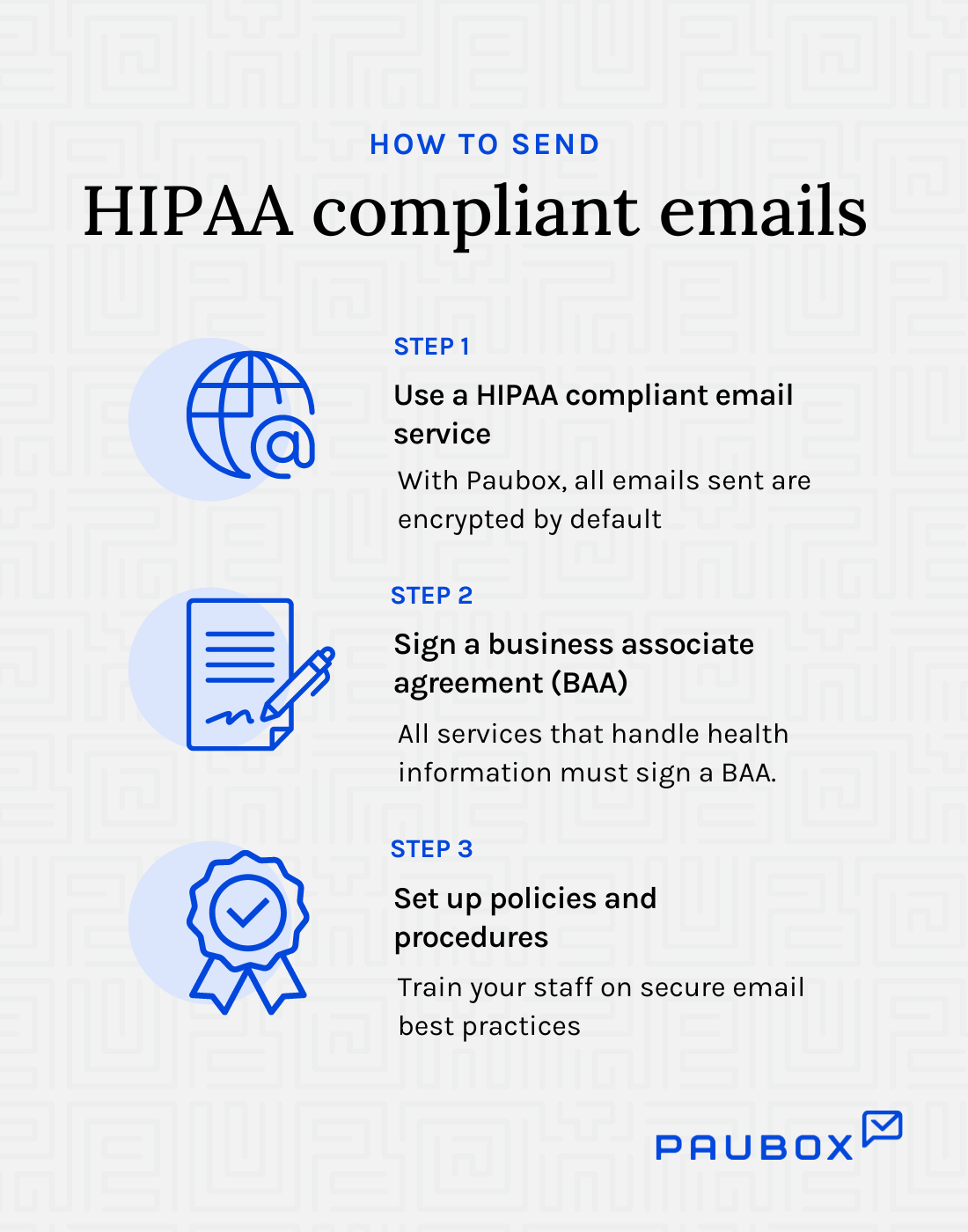
Four steps to send HIPAA compliant emails
1. Secure patient information in transit and at rest
To ensure HIPAA compliance when sending email, use secure email solutions that encrypt messages and attachments in transit and at rest.
IT professionals at larger healthcare organizations may have the resources to manage their own email servers, but the quickest way to ensure you're sending HIPAA compliant emails is to use a HIPAA compliant email solution.
Why it matters: A good email solution will be easy to set up and work with your existing email client, like Google Workspace or Outlook. This minimizes disruption and training needs.
2. Enter into a Business associate agreement
A business associate agreement (BAA) is a written contract between a covered entity and a business associate. It is required by law for HIPAA compliance.
Why it matters: Even if your emails are encrypted, you still need a signed BAA with your email service to comply with HIPAA regulations.
Learn more: Business associate agreement provisions
3. Set up policies and procedures
Policies related to PHI access, storage, and disclosure should be in place to limit access to authorized individuals only. This includes specific guidelines for the use of email to transmit PHI, including requirements around encryption, access controls, and secure transmission.
Why this matters: An internal policy for HIPAA compliant email ensures all employees know their responsibilities regarding handling and transmitting PHI electronically.
4. Train your staff on secure email best practices
In addition to having policies around HIPAA compliant email, healthcare organizations should train employees on these policies and procedures.
Why this matters: Training staff can help prevent accidental or intentional violations of HIPAA regulations when sharing PHI through email.
Are Gmail, Microsoft 365, and other email clients HIPAA compliant?
Is Gmail HIPAA compliant?
Basically, yes, if you use Google Workspace. A free Gmail account is not HIPAA compliant.
To send HIPAA compliant emails with Google:
- Pay for Google Workspace to eliminate ads and secure your data from automated processing.
- Sign a BAA with Google.
- Use a third-party solution like Paubox Email Suite to ensure HIPAA compliance for all sent emails.
Learn more:
Is Microsoft 365 HIPAA compliant?
Microsoft 365 provides access to a suite of productivity tools, including Windows, Office applications (Word, Excel, PowerPoint, etc.), email, and storage (OneDrive).
“The Microsoft HIPAA Business Associate Agreement is available through the Microsoft Online Services Data Protection Addendum by default to all customers who are covered entities or business associates under HIPAA.”
Microsoft 365 is HIPAA compliant, and there are no additional steps to take to obtain a BAA with Microsoft.
Quick tip: Outlook, the desktop email software, can be configured to send HIPAA compliant email with Paubox.
Learn more:
- Is Microsoft 365 HIPAA compliant?
- Microsoft in-scope cloud platforms & services
- How do I sign a BAA with Microsoft? (2023 update)
Are Yahoo, Hotmail, and others HIPAA compliant?
Yahoo, Hotmail, and other free email clients don't sign business associate agreements. Without a BAA, even if the email is encrypted, HIPAA guidelines don't consider it in compliance.
The bottom line: Before sending any patient data, get a BAA signed by whichever email service you use. However, it's unlikely that a free email service like Yahoo or Hotmail will sign a BAA.
HIPAA compliant email checklist
To know if an email is HIPAA compliant, you should look for the following elements:
[] Business associate agreement: A BAA is required to send HIPAA compliant email
[] Access controls: Only authorized individuals can access the information.
[] Secure transmission: The email should be transmitted securely over the internet, typically using Transport Layer Security (TLS) encryption. Confirm this by checking email headers. If the email is encrypted, you may see headers that indicate that the message was transmitted using TLS encryption.
[] Proper identification: The email should identify the sender and recipient of the message.
In the know: TLS 1.0 and TLS 1.1 are no longer considered secure. TLS 1.3 is the newest and most secure version of the TLS protocol and provides increased privacy compared to previous versions of TLS and non-encrypted SMTP email. Read more about NSA guidance and TLS.
Learn more: HIPAA compliant email checklist 2024: What you need to know
Which emails should be HIPAA compliant?
Any email that contains Protected Health Information (PHI) must be HIPAA compliant. This includes:
- Emails between healthcare professionals: Emails between healthcare providers (e.g., doctor to doctor) discussing a patient's medical condition, treatment, or medication must be encrypted.
- Emails to business associates: Emails to business associates and vendors containing patient information must be encrypted. Additionally, a signed BAA must also be in place.
- Internal organization emails: If your organization's servers are secure, you don't need to encrypt emails specially. However, you should encrypt all emails if you have remote access (like work-from-home employees). It's best to encrypt emails internally and externally to avoid human error due to different email processes.
- Healthcare Newsletters: If your healthcare organization or practice sends newsletters, it's best to encrypt them. HIPAA compliant email marketing can be a gray area, but even marketing treatment can be considered protected patient information.
- Personal emails: It violates HIPAA guidelines to send any patient information unencrypted. So any healthcare professional that works on their personal computer and emails PHI must still ensure HIPAA compliance.
- Emails from patients: HIPAA regulations do not specifically require incoming emails from patients to be encrypted, but covered entities must still protect any PHI received.
Learn more:
FAQs
Do attachments need to be encrypted?
Yes. HIPAA compliant email solutions like Paubox will encrypt attachments in transit.
What's the difference between encrypted, secure, and HIPAA compliant emails?
Encrypted emails are scrambled in a way that makes them unreadable by unauthorized individuals.
Secure email refers to emails transmitted over the internet using encryption and other security measures to protect the information from interception or tampering.
HIPAA compliant email refers to emails that meet the specific requirements outlined by HIPAA regulations for the handling and transmission of Protected Health Information (PHI). This includes requirements for encryption, access controls, and secure transmission methods.
When does liability end when sending protected health information?
Once a HIPAA compliant email is received by the patient or business associate, the healthcare professional who sent the email is not generally held liable for any unauthorized access or disclosure of PHI.
However, the healthcare professional may still be responsible for ensuring that the email was encrypted correctly and transmitted according to HIPAA regulations to protect the privacy and security of the PHI.
Does the subject line of an email have to be encrypted?
Since even just a name or email address, when coupled with an email from your practice, can be considered PHI, email subject lines must also be HIPAA compliant.
Note: When you send an email to a patient using most portal-based encrypted email products, only the message in the email portal is guaranteed to be secure, not the email alerting the patient that they have a message waiting.
Do I need to use portals to share PHI?
No. In fact, portals have several issues that add risk and complexity. HIPAA compliant email solutions are an accepted (often better) alternative to portals. Read more about portals vs. encrypted email.
Email vs. portals: The use of portals has several disadvantages:
- Patients prefer email - 93% of patients want to email their doctors
- Portals require additional steps, passwords and are technically more challenging
- Email doesn't require additional staff training
- Email is easy to use on any device
Go deeper: Do you need an email portal to be HIPAA compliant?
Do my patients need to encrypt their emails?
HIPAA regulations do not require patients to encrypt their emails. However, covered entities and business associates must still ensure that any PHI they receive from patients is protected.
Is patient consent needed to transmit PHI through HIPAA compliant email?
Patient consent is not required to transmit PHI through HIPAA compliant email. However, patients have the right to be informed about safeguards and to request alternative transmission methods if email transmission is not secure or feasible.
Other HIPAA rules around handling ePHI
Email retention: HIPAA requires covered entities and business associates to retain emails containing electronic Protected Health Information (ePHI) for six years and to implement policies and procedures for the secure retention and disposal of ePHI.
Incoming emails: Incoming emails containing PHI must be identified, handled, and stored securely within HIPAA requirements.
Password requirements: HIPAA requires policies and procedures for secure password selection and management, including:
- Use unique user IDs and passwords to access ePHI.
- Require strong passwords with a minimum length and complexity.
- Change passwords regularly, and do not reuse old passwords.
- Disable access to ePHI in the event of a workforce member termination or change in job duties.
- Limit password attempts to prevent brute-force attacks.
- Encourage the use of multi-factor authentication to enhance security.
Does HHS Notification of Enforcement Discretion apply to sending PHI via email?
The HHS Notification of Enforcement Discretion is a temporary policy that allows certain HIPAA violations to be waived during the COVID-19 public health emergency.
The policy was understood to apply to telehealth and remote communication but does not explicitly apply to email. Transmitting patient information must still be encrypted.
Safeguard patients
At heart, sending HIPAA compliant emails is crucial to safeguard patients' sensitive medical information. By following the guidelines and implementing appropriate measures, covered entities, and business associates can maintain regulatory compliance and uphold the trust of patients and partners.
Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.



 Dean Levitt
Dean Levitt


