It looks like someone has evidence of your latest traffic violation. All you have to do to see it is click on the link.
Of course, clicking the link won’t reveal your shameful transgression. It’s just another phishing attack attempting to install a Trojan on your system, probably ransomware.
And the experts at the Cybersecurity and Infrastructure Security Agency (CISA), together with colleagues at the Federal Bureau of Investigation (FBI), say the culprit is a familiar one.
What happened?
The CISA and FBI have issued a new joint advisory about a sophisticated group of cybercrime actors that’s luring victims, via phishing emails, to steal sensitive information.
The weapon of choice is called TrickBot, which was first detected in 2016.
The advisory outlines many different ways TrickBot can be used to compromise a corporate network, provides code signatures to detect it, and outlines best practices to protect company systems and prevent attacks.
What is TrickBot?
TrickBot started out as a fairly simple weapon wielded against financial institutions. But it evolved quickly.
One year later, TrickBot had been modified to attack corporate customer relationship management (CRM) software, PayPal accounts, and Coinbase accounts.
By 2019, TrickBot had countermeasures built in to prevent detection by security software, while it expanded its menu of targets to include mobile phone carriers, Microsoft Windows networks, and encryption keys. Most recently, Trickbot gained the ability to compromise Linux systems and Android mobile devices.
The ways Trickbot tricks victims has evolved with the times as well. In 2019, the hook was a claim that the recipient was named in a sexual harassment case. Last year, it made headlines as the most common source of COVID-19 pandemic-related phishing attacks. This most recent round targets insecure drivers.
What can TrickBot do?
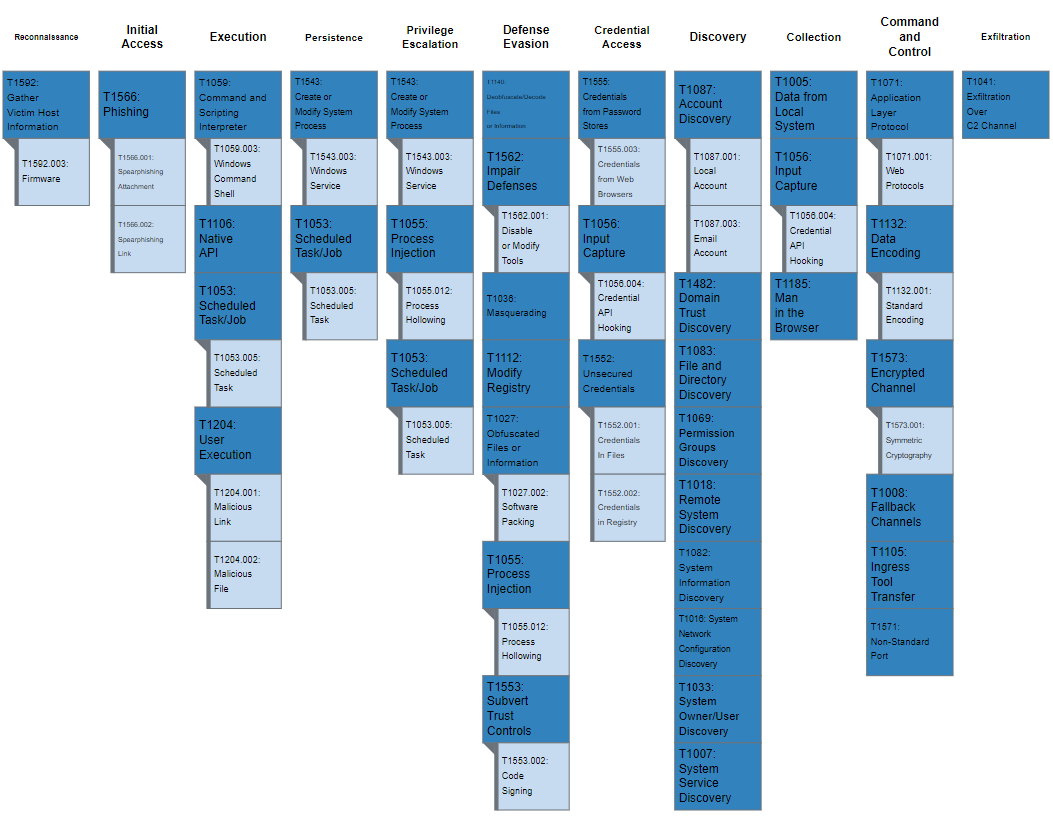
TrickBot is no longer a rough blob of JavaScript code. According to the CISA-FBI announcement, “TrickBot has evolved into highly modular, multi-stage malware that provides its operators a full suite of tools to conduct a myriad of illegal cyber activities.” The advisory included this illustration of TrickBot’s bag of tricks:

Internet security company ESET has catalogued over 40,000 TrickBot configuration files for at least 28 individual plugins used by the malware to steal data, spread across networks, and defend itself against cybersecurity countermeasures.
Attackers use TrickBot as a gateway to install other malicious software, including Emotet out of Russia, Ryuk, and Conti. It steals information through man-in-the-browser attacks, and can even use victim machines to mine cryptocurrency.
Who is being targeted by TrickBot
While TrickBot started in the financial sector, its favorite targets today are hospitals and healthcare systems.
In September 2020, an international network of over 400 healthcare facilities was knocked offline when TrickBot was used to install Ryuk ransomware. The next month, a joint CISA-FBI advisory warned of “an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers,” providing guidance to the Healthcare and Public Health (HPH) Sector.
“These issues will be particularly challenging for organizations within the COVID-19 pandemic,” the advisory noted. “Administrators will need to balance this risk when determining their cybersecurity investments.”
This latest alert, however, does not mention healthcare or any other specific industry.
How do you stop TrickBot?
The CISA-FBI joint advisory lists nearly two dozen recommendations to businesses and other entities to strengthen the security posture of their organization.
Number one on the list is providing social engineering and phishing email training for employees. Using two-factor authentication is also recommended.
For additional reading, there’s CISA’s Technical Approaches to Uncovering and Remediating Malicious Activity. And the advisory also recommends that system administrators reference a special publication of the National Institute of Standards and Technology, “Guide to Malware Incident Prevention and Handling for Desktops and Laptops.”
How can Paubox help?
The weakest link in the security chain is often employees, and the most common attack vector is email. In addition to training, robust email security is a must.
Our HIPAA compliant email solution, Paubox Email Suite Plus, is HITRUST CSF certified, and works with popular email providers like Microsoft 365 and Google Workspace. It blocks malicious emails before they ever reach an employee’s inbox.
Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.



 Hoala Greevy
Hoala Greevy


